This article shares the core differences between Software-Defined Perimeter (SDP) and Virtual Private Networks (VPN). Yes, you will find the SDP vs VPN guide.
Remote work has increased massively in today’s world. Previously, it was primarily exclusive to the sales personnel and field technicians who provided their services by connecting to company resources via virtual private networks.
But the post-pandemic organizational system has seen the rise of remote work across diverse sectors globally. According to NorthOne, 58.6% of the American workforce currently works remotely. A far cry from the 4.7 million US employees who worked from home before the pandemic.
These development demands on network security are massive. Such requests require a solution that supports an undefined perimeter as resources are moved to the cloud for safer and smoother collaboration among a diversified workforce.
Overblown malware attacks and data leaks became a constant challenge for security managers who had to minimise the dangers posed by the new wave of a diversified workforce. And for more effective solutions compared to popular VPNs, Software Defined Perimeters (SDPs) are being deployed to help IT teams rise to security issues.
Definitions
What is a Software-Defined Perimeter (SDP)?
Software-Defined Perimeter is a method of fixing network security issues by creating segmentation and user or device authentication to control access to a network. The technology used in the creation was originally an idea by the US Defense Information Systems Agency (DISA), developed in 2007 as a powerful security solution for monitoring access to complex cloud-based systems.
It controls access to resources using the least-privilege model while also creating avenues for administrators to customize and effect security policies.
SDP focuses on positioning the network perimeter on software instead of hardware and making a company’s assets practically invisible to external access, whether hosted in the cloud or on-premise. However, validated users will be able to access resources.
This hardware-less technology makes network security flexible and avoids the weaknesses of popular security solutions.
How Does SDP work?
SDP can be illustrated as a door to a home with numerous assets left on lock and key to outsiders. Any visitor trusted to receive access must first be given entry by an insider, after which the door is locked up again.
This illustration means that when an organization has an SDP in place, it should be practically impossible for an outsider to connect to the server if he hasn’t been authenticated.
However, when a validation process is positive for a user and their device, rather than connect them directly to the more extensive network, an individual network connection is generated in their favour to link their device with the server they are accessing.
Software-Defined Perimeters contain an organization’s network resources in a secure firewall network. The SDP software foundation secures connections built to both cloud services and local resources from external access. It also leverages manipulation of the SDP controller to determine the kind of resources that can be made available to potential users when once they are authenticated.
What is a Virtual Private Network (VPN)?
A VPN is an encrypted network built over an unencrypted network to secure the user’s connection. It privatizes the connection between a user’s device and the internet. So, it becomes secure and inaccessible to unauthorized individuals.
In simple words, when you connect to the internet via a VPN, all your data traffic is channelled over an encrypted virtual tunnel, making your IP address difficult for anyone to trace. Therefore, your connection is invisible to other internet users. It also frustrates potential cyber-attacks that would have been directed toward your access.

In addition, with an encrypted tunnel, you will be able to view restricted content from different parts of the world. For instance, streaming services often limit their content to selected locations across the globe. With a VPN, you can view the content in those authorized areas.
VPNs are traditionally used to build a secure connection between a remote employer and a company’s network. However, SDPs can be considered in place of VPNs in some instances.
How Does a VPN Work?
A VPN permits a network redirection for a user through a remote server operated by a VPN host. It is specially configured to conceal your identity and encrypt your connection.
So, while accessing the internet, the VPN server becomes your data source. Hence, you become invisible to third parties, including your Internet Service Provider (ISP), making it hard to monitor your activities on the internet. And even if anyone was to lay hold of your data, they’ll not find it helpful.
SDP vs VPN: What Are The Differences?
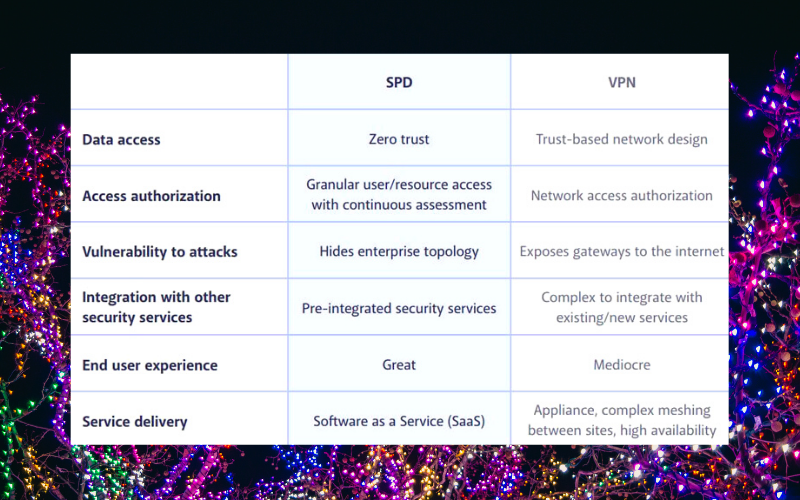
Both SDPs and VPNs encrypt users’ data. However, they build connections in different ways. VPNs allow users to access all organization data once authenticated, while SDPs restrict users to resources per session.
In terms of policy automation, it is rarely achievable with VPNs, but SDPs make it functional. Other SDP vs. VPN differences include:
Environment of Operation
SDPs offer extensive flexibility of operation, focusing on software instead of hardware like VPNs. Their deployment can be done both in the cloud and on-site. And offer users the opportunity to connect from the home, office, or any location.
Security Enforcement
Indeed, VPNs allow all connected users to access all available resources on the network. Similarly, SDPs can implement a Zero-trust model where requests are considered unsafe and a potential threat until they are authenticated. If users are not verified, they will not access resources. In addition, a connection is limited to assets allocated to them per time. Hence, SDPs are more secure.
Remote Service
Considering how different stakeholders in an organization interact today. Yes, it is widely unpredictable and widens the threat surface for cybercriminals to implement their plans.
VPN-encrypted tunnels are a secure way to build connections; however, intruders will successfully steal proprietary data from sources if they get compromised. So, users must be trusted enough to deploy the latest tools every time they have to build connections. On the other hand, SDPs will offer high convenience and well-suited security combinations for remote workforces.




Comments are closed.